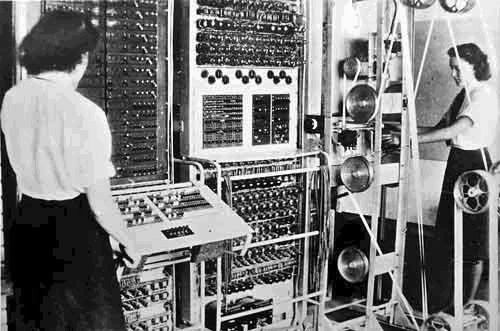
Figure 1 – Mark 2 Colossus computer that was used on the high level Lorenz Cipher code named Tunny by the British at Bletchley Park. This artistic work is from the Wikipedia and because it was created by the United Kingdom Government before June 1, 1957 is in the public domain.
I wanted to continue today our discussion of the “cyber other.” The “cyber other” is a kind of alter ego universe of man-machine that we have created. We call it the internet and we are increasingly allowing this abstraction to control our world. So let’s begin in the beginning. Figure 1 is historic. It shows a Mark 2 Colossus computer. The ten Colossi were the world’s first (semi-) programmable electronic computers. The earliest dates from 1943, and these were used by the famous World War II code breakers at Bletchley Park. Essentially Figure 1 captures the birth of the internet, the birth of the “cyber other.” And really it represents the first salvo in the future of warfare – cyber warfare.
Well the good news is that it does not appear that the 2016 US Presidential Elections were hacked.
The bad news lies is in two quotes. First we have that when asked if she ever wiped her email server clean, Hillary Clinton jokingly responded “
But I will point out that candidate Hillary Clinton is now yesterday’s news, and at some point Trump supporters are going to realize that no one any longer cares about what they think about her, but rather what they have wrought upon us. Which brings us to the really bad news.
“I notice, anytime anything wrong happens, they like to say the Russians are — she doesn’t know if it’s the Russians doing the hacking. Maybe there is no hacking. But they always blame Russia. And the reason they blame Russia because they think they’re trying to tarnish me with Russia. I know nothing about Russia. I know — I know about Russia, but I know nothing about the inner workings of Russia.”
This friends was candidate Trump on the impending cyber war and we are forced to hope that President Trump isn’t candidate Trump but rather some kind of great chameleon savior. But regardless, the next world war started with Figure 1. It is to be a cyberwar and, prepared or not, it is coming.
In June of 2010 it is reported that Stuxnet, a 500-kilobyte computer worm infected the software of at least fourteen industrial sites in Iran, including a uranium-enrichment plant. And it is widely believed this blew up enrichment centrifuges by throwing them out of balance. The government of Iran has not confirmed this event and it is variously thought to be the work of the US and Israeli intelligence. It really doesn’t matter. The point is … Here is a link to a list of the twenty-five biggest cyber attacks: The Canadian Government, the Indian Government, Paypal, the Church of Scientology, Citigroup… The hackers are flexing their muscles like a newborn creature in the movie Aliens. And it is important to say that I know that you Apple users think you are immune. You are wrong, bigly!
The more we tie ourselves to the “cyber other,” the more vulnerable we become. And tie is the right word. The “cyber other” has become real and tangible. Vulnerability is why scientists are so fearful of scientifically ignorant and denying politicians: the creationists, the disbelievers in climate change. The growth of the “cyber other” and our connectivity with it is inevitable and truly unstoppable. It is time to forego “old time religion” in favor of informed government. We should approach the coming cyberwar with the singular goal, winning.
